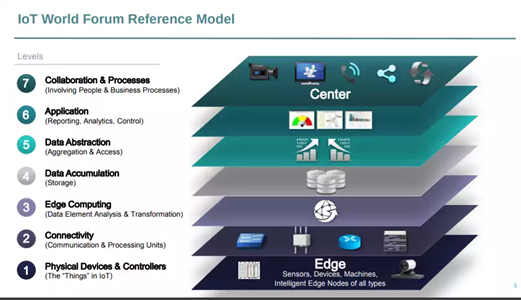
Figure 3: 7-layer reference model
The elements of the simple three-layer architecture described earlier can be perceived in this framework: the physical devices and controllers in the perception layer, the communication resources in the connectivity layer, and the analytics and control software of the application layer, with the additional edge computing layer, data accumulation and abstraction layers, and the process and collaborative tools of the business layer.
Compared with the simpler architectures, the edge layer included in the more sophisticated models has been central to enabling IoT deployments to meet the needs for increased functionality and performance, faster response, reduced power consumption, and greater data privacy. By filtering and processing information early, in a location close to its point of capture, low latency and real-time determinism is possible. Only a subset of the data captured is sent to cloud services, which also saves network bandwidth and storage as irrelevant data is discarded before being sent to the cloud.
The IoTWF 7-layer visualisation of IoT architecture facilitates a tiered approach to security that is enforced at the transition points between levels.
Devices and controllers in the perception layer can be physically accessible, as well as addressable via a network connection, making them vulnerable to threats such as tampering, theft, or unauthorised manipulation by loading malicious code, stealing security keys, or other secret information such as passwords.
Other vulnerabilities include a lack of data authentication, which becomes apparent at the data-accumulation layer where data collected from sensors or devices can be susceptible to spoofing or tampering. Moreover, data transmission between devices or gateways can be intercepted or accessed by unauthorised parties if not properly encrypted.
From the standpoint of the abstraction layer, inadequate access controls may allow unauthorised parties to gain access to sensitive data or perform unauthorised operations. Also at the abstraction layer, inadequate validation of incoming data may lead to the ingestion of malicious or malformed data, potentially compromising the integrity and security of the system.
In the application layer, vulnerabilities in APIs or other application interfaces may allow attackers to exploit weaknesses in the system, leading to unauthorised access, data leakage, or service disruptions. Also, insecure coding practices such as insufficient input validation or buffer overflows can introduce vulnerabilities that attackers can exploit to compromise the system.
Weak or ineffective authentication and authorisation mechanisms can allow unauthorised access to applications or data, leading to potential security breaches.
A lack of robust monitoring and logging mechanisms can make it difficult to detect and respond to security incidents or identify potential vulnerabilities. This can become apparent at the process layer. In addition, insufficient security awareness and training among personnel involved in the operation and maintenance of IoT systems can increase the risk of human error or oversight, leading to security vulnerabilities.
Implementing robust security measures, such as strong authentication, encryption, access controls, secure coding practices, and ongoing monitoring, is crucial to mitigate these vulnerabilities and ensure the security and integrity of IoT systems.
Conclusion
An IoT deployment may be simple in concept, although the implementation can be complex; potentially involving large numbers of nodes that can be dispersed over a geographically large area. A framework that describes the architecture in adequate detail can guide development by helping teams to make sure all the functional aspects are met and all security issues are handled properly.
More from this series:


